0 Preface
With the rapid development of mobile communication technology, people can access the network for transaction and data exchange anytime and anywhere by means of terminal equipment, which promotes the development of mobile e-commerce. As a major development direction of mobile communication applications, mobile e-commerce has many advantages compared with online transactions on Internet, so it has attracted more and more people's attention. The security of mobile transaction systems is a key issue that must be solved to promote mobile e-commerce.
In the wired network environment, PKI is the foundation and core of network security construction, and is the basic guarantee for the implementation of e-commerce security. However, the limitation of bandwidth and terminal processing capability in the wireless communication network makes the PKI unable to be introduced into the wireless network. wPKI (wirelesS PKI) is developed to meet the security needs of wireless communications. It can be applied to wireless devices such as mobile phones and PDAs to provide users with identity authentication, access control and authorization, transmission confidentiality, data integrity, non-repudiation, etc. Security service. The smart card has excellent security and can be used as a good access carrier for the network security client in the WPKI system. The smart card has its own processor, enabling cryptographic algorithms and digital signatures to be implemented within the card and securely storing the private key. At present, smart cards have been gradually applied to public security system police inquiry, tax department inquiry, enterprise mobile application, mobile e-commerce, mobile e-banking, etc., including USB key based on PKI system and STK for mobile service processing using mobile phone short message. Card and so on.
1 WPKI and PKI smart card
The WPKI consists of a terminal, a PKI portal, a CA, a PKI directory server, and the like to form a key management system. In the application of WPKI, service devices such as WAP gateways and data providing servers are also designed. The basic structure of WPKI is shown in Figure 1.
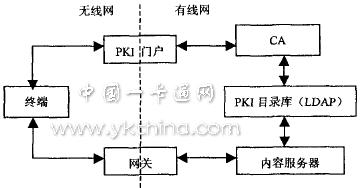
Figure 1 Structure of W PKI
The WPKI defines a component that is not in the PKI, the PKI portal, which handles requests from terminals and gateways. The PKI portal generally represents the RA and is usually integrated with the gateway. RA is the bridge between the connection terminal and the gateway. It is responsible for accepting the registration request of the terminal and the gateway, and registering the certificate with the CA. On the one hand, the CA needs to put the generated certificate into the certificate directory (such as the LDAP server) for the need ( For example, when devices such as gateways and servers need to be authenticated, each entity queries; on the other hand, the certificate is sent to the terminal and gateway through the RA. The terminal includes a WAP device such as a mobile phone or a PDA, and the smart card applied thereto is used to store confidential information such as a digital certificate and a key, and implements functions of encryption and decryption and digital signature.
A smart card consists mainly of a microprocessor (CPU) and memory and an operating system that is fixed on the card. It is an integrated circuit chip card with storage capacity and computing power. -2] PKI smart card is the product of applying PKI technology to smart cards. In the PKI system, private keys and digital certificates issued by third-party certification authorities can be stored on extremely secure smart cards. Since the microprocessor carried by the smart card can implement functions such as storage, encryption and decryption, and generation of a key pair in the card, the digital signature can be automatically calculated and generated by using the private key stored on the smart card. The entire signature process is automatically completed by the card, and the signature key cannot be issued, so the PKI smart card can effectively ensure the security of the private key and the validity of the signature.
2 Analysis of application problems of smart cards in WPKI
The security of a secure and reliable WPKI application depends on all aspects of the system. When a smart card is applied to a WPKI, it plays an important role in the security of the client. The WPKI system optimizes the PKI according to the differences between the wireless environment and the wired network. When the smart card is applied to it, since the smart card has special environmental requirements, some special problems need to be solved. In the smart card application system, the terminal can support multiple application systems. The smart card on the terminal needs to save all the application system CA public keys supported by it, generate keys and perform encryption and decryption operations, digital signatures, and store digital certificates. Therefore, the secure storage of keys on smart cards is an important issue to be solved. In the interaction between the smart card and the terminal, it is also necessary to perform corresponding information authentication and save the interactive information to determine the legality of the smart card and the terminal.
In addition, as a carrier of some confidential information, the smart card itself is also a key factor in the security of the whole system. Therefore, the security policy and security components are required in the design and selection of the smart card to achieve a certain level of security.
2.1 Smart Card Key Management Strategy
Public key cryptography has become the cornerstone of modern network security technology. Currently, there are two public key cryptographic algorithms at the core, namely RSA algorithm and elliptic curve (ECC) algorithm. When a smart card is applied to a WPKI, it is not only necessary to select an algorithm that is simple to calculate and high in security, but also important for the management of the key.
2.1.1 Algorithm selection
In PKI-based applications, the security of the key algorithm is also a very important part. Currently, smart card chips usually provide encryption/decryption computing capabilities of DES and even Triple-DES. The DES algorithm is a public algorithm that, although decipherable, is neither economical nor practical. For example, the best attack on a 16-round DES using differential analysis requires 24r to select plaintext, and the best linear attack requires an average of 245 known plaintexts.
The advantage of the RSA algorithm is that it is simple and easy to use. The disadvantage is that as the security requirements increase, the key length required is almost doubled. At present, it is generally considered that the RSA key has a length of at least 1024 bits or more, but the 1024-bit encryption operation is a heavy burden for the smart card. The ECC algorithm uses the shorter key to achieve the same encryption strength as the RSA algorithm. Its number theory is based on the elliptic curve discrete logarithm problem on the finite field. There is no sub-exponential time algorithm for this problem, so the ECC algorithm Has the highest security strength per bit. Due to the limitations of CPU processing power and RAM size, a smart key cryptosystem with a small amount of computation and high encryption strength is crucial for implementing digital signature applications on smart cards. ECC has obvious advantages in this respect. The security of 160-bit ECC algorithm is equivalent to the 1024-bit RSA algorithm, and the 210-bit ECC is equivalent to 2048 bits of RSA.
The encryption and decryption of the secret data by the smart card is completed in the card, and the attacker cannot obtain the secret data through the smart card interface, so it is relatively safe.
2.1.2 Key Storage
The wireless identity module (WIM) is used to store key information such as the WPKI public key and the user private key and related certificate information to complete the security functions of the wireless transmission security layer (WTLS), the transport security layer (TLS), and the application layer. j. In the implementation of WIM, the most basic requirement is the anti-aggressiveness of its carrier, that is, there is some physical protection measure, so that any operation to illegally extract and modify information from the WIM module cannot be successful. The smart card is a very A good kind of security carrier (the SIM card is commonly used to implement this module), and the smart card has its own processor for encryption and decryption and digital signature, which saves resources of terminal devices such as mobile phones. In general, public keys have two types of uses: digital signature verification and data encryption. Therefore, the terminal smart card needs to configure a signature key pair and an encryption key pair. These two types of key pairs have different requirements for key management.
The signature key pair is generated by the terminal smart card. The public key is sent to the authentication center CA. The CA creates the certificate and sends it to the user. The private key is stored in the smart card and cannot be read by the WAP terminal device or backed up.
Encryption key pair: Generally, the client encryption key is generated by the CA center. After the generation, the public key user issues a certificate. When decrypting, the CA center encrypts and saves it, that is, performs backup processing. When the smart card is personalized, the decrypted private key is written into the card in an encrypted manner, and the encryption certificate is completed at the same time.
Pet bags or carriers in different material, such as fabric, plastic, or on wheels are getting popularity around the world. Sometimes dogs are required to be carried in carriers on public transportation or just easier to bring your dogs around to keep them calm in new or loud environment.
We have pet sling bags that allow you to take care of your pet like a baby while you walk or exercise.

You can use our pet backpacks to carry your pets on your back or front liked carrying your school bags at all times.
Wheel mobiles are designed for pet traveler who wants a smaller mobiler and can be pulled or pushed easily in 360 degrees while walking in the crowd.

Pet strollers are a more extensive carrier that you can bring a few of your dogs together in a trip. And also keep your other belongings on the stroller to save you strength for the walk.
Pet folding carriers are space saving carrier that can be stored and assembled easily in a few minutes with a zipper.

There are many other kinds of carrier available in our range. Please find out more on our site.
ABOUT US
PERCELL PET is established in 1978 with offices located in Taipei, Taiwan and Guangdong, China. Currently, Percell Pet partners with more than 49 distributors around the world and carries thousands of quality pet supplies for dogs, cats, birds, fresh and salt water fishes, reptiles and small animals, like rabbits and ferrets, etc from Taiwan and China.
We supply popular and classic pet products around the world and also OEM products at your needs.
- FLEXIBLE IN ORDER VOLUME, orders can be done in LCL or full container, MOQ can be discussed accordingly.
- COMMUNICATION, staff are fluent in written English with in time replies.
- SERVICE, provide help and solutions to your sourcing in Taiwan and China.
Travelling Pet Backpack, Durable and Colorful Pet Backpack,Outdoor Pet Backpack,Lilac Pet Backpack
PERCELL PET SYSTEM CO., LTD , https://www.percell-pet.com